Tag: Products
-

Put PICA on Notable Events
For every notable event, the analyst adds a little PICA. What’s a notable event? It’s more than a record that something happened, or an alert that something is expected to happen. It requires some form of response, from “read and move on” to “read and acknowledge” to “follow this run…
-

Managing the Unmanageable
I’ve been thinking off and on about containers (FKA partitions, zones, jails, virtualized apps) and mobile ecosystems for a few years. These technologies have gone through several iterations, and different implementations have different goals, but there is an overlap in the currently extant and growing versions. Hold containers, IOS/Android, and…
-

Multi-tenancy in platforms
If you’ve built a monolithic enterprise product, it is not sensible to convert it to multi-tenancy. You can sell a managed service provider (MSP), but you’re not going to get to software as a service (SaaS). Often no one wants to discuss reasoning at all, because the need to convert…
-

Supporting Ancient Software
With another round of fixes to Windows XP, the time is ripe for bloviating about supporting ancient stuff. Every software vendor has to decide what to do about supporting what they used to ship, as well as the broader ecosystem around them. Operating systems, databases, service providers. Maximize use of…
-
What does your product disallow?
Product design sometimes opens an interesting can of worms: things that may be possible to do, but which the designer didn’t intend. Do you hide these paths or not? Will your user ultimately be frustrated, or satisfied? The answer depends on whether your product’s design accurately sets and meets expectations…
-
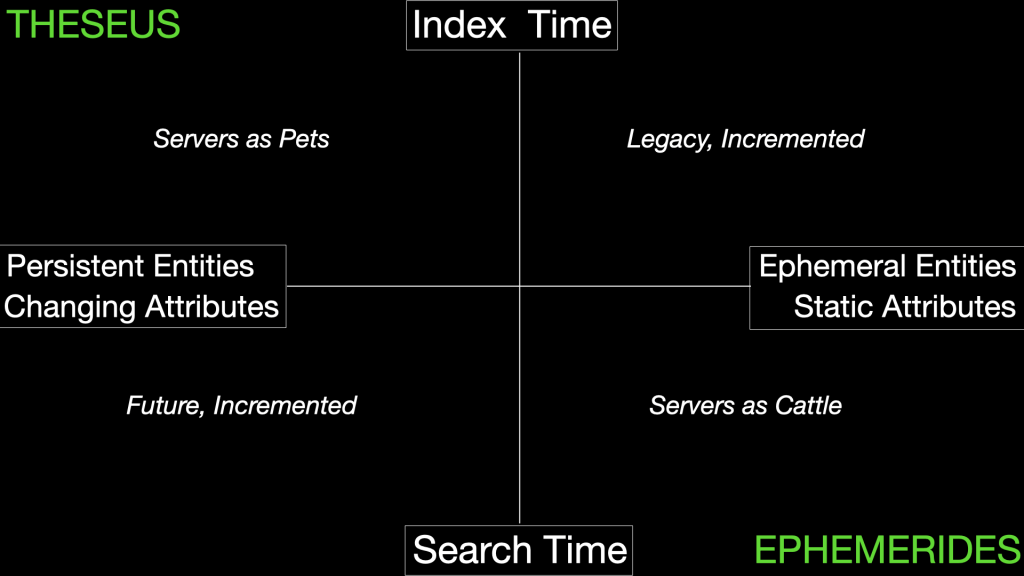
Entities and Attributes
Quadrant models are useful organizing tools. Let’s use one to look at the problem of managing the attributes of entities in systems visibility. I’m not expecting to solve the problem, just usefully describe the playing field. Horizontal axis:* persistent entities with changing attributes* ephemeral entities with static attributes Vertical axis:*…
-

Moving the transformation point of data
There’s a pattern that has become common knowledge, perhaps on its way to received wisdom. Endpoints pass their raw data off to storage as quickly as possible. Analysts then do their work against that storage using map reduced processors, automated and/or ad hoc. This pattern has many benefits and is…
-

DURSLEy and CAPS
Monitoring and metrics! Theoretically any system that a human cares about could be monitored with these three patterns: I’m hardly the first to notice there’s overlap… here’s a good starting point to read from. I haven’t seen these compressed to a single metric set yet, probably from not looking hard enough.…
-

Licensing thoughts, round two
License Models Suck got a lot of interesting conversations started (and there’s a roundup page), time to revisit from the customer’s perspective. Let’s also be clear, this is enterprise sales with account reps and engineers: self-service models are for another day. As a vendor, the options I describe seem clearly…
-

Phases of Data Modeling
Say that you want to use some data to answer a question. You’ve got a firewall, it’s emitting logs, and you make a dashboard in your logging tool to show its status. Maybe even alert when something bad happens. You’ve worked with this firewall tech for a few years and…
