Tag: Operations
-

What Should Go Into a CMDB
It’s not every day that information technology work leads you into philosophy, but designing a configuration management database will do it. Spend a little while thinking about what is known or even knowable about the services you’re trying to provide and the entities that compose them, maybe you’ll end up…
-

Two Types of Questioning
Answers to questions can easily fit into two flavors: operationalized and free-form. Classify the use cases: there’s the questions you know how to ask, and the questions you don’t know to ask yet. A question that you know how to ask is operationalized. You’re looking for yes, no, or broken,…
-

Data Value and Volume are Inversely Proportional
In 2006, Clive Humby coined the phrase “Data is the new oil”. This is often misinterpreted as “Data powers the economy”, particularly by folks who sell data processing and storage, but it’s useful to see what someone who actually uses data says. In 2013 Michael Palmer, of the Association of…
-

Penny Wise Hardware
Thesis: Organizations will continue to squeeze their highly paid people into the worst possible computing environments in order to block any accidental efficiency that might evolve in their organizations. Evidence to support that thesis: Of course the thesis is silly, no one really means to starve their organization. It just…
-

Consulting’s Bad Rap
Naming no names… but there’s a type of management consulting shop with an unsavory reputation among middle managers and individual contributors. Let’s look at how the reputation is earned: by training to a model that produces failure as often as not, but always successfully deflects blame. It’s easy to find…
-
Know everything, then automate!
The concept of virtual patching has set me off on a small rant. If you’re not familiar, the concept is something like this: vulnerability scanners determine that PC42 in the CritStuff system has a nasty problem, but you can’t patch it for reasons. So instead, software magically figures out that…
-

Put PICA on Notable Events
For every notable event, the analyst adds a little PICA. What’s a notable event? It’s more than a record that something happened, or an alert that something is expected to happen. It requires some form of response, from “read and move on” to “read and acknowledge” to “follow this run…
-

Managing the Unmanageable
I’ve been thinking off and on about containers (FKA partitions, zones, jails, virtualized apps) and mobile ecosystems for a few years. These technologies have gone through several iterations, and different implementations have different goals, but there is an overlap in the currently extant and growing versions. Hold containers, IOS/Android, and…
-
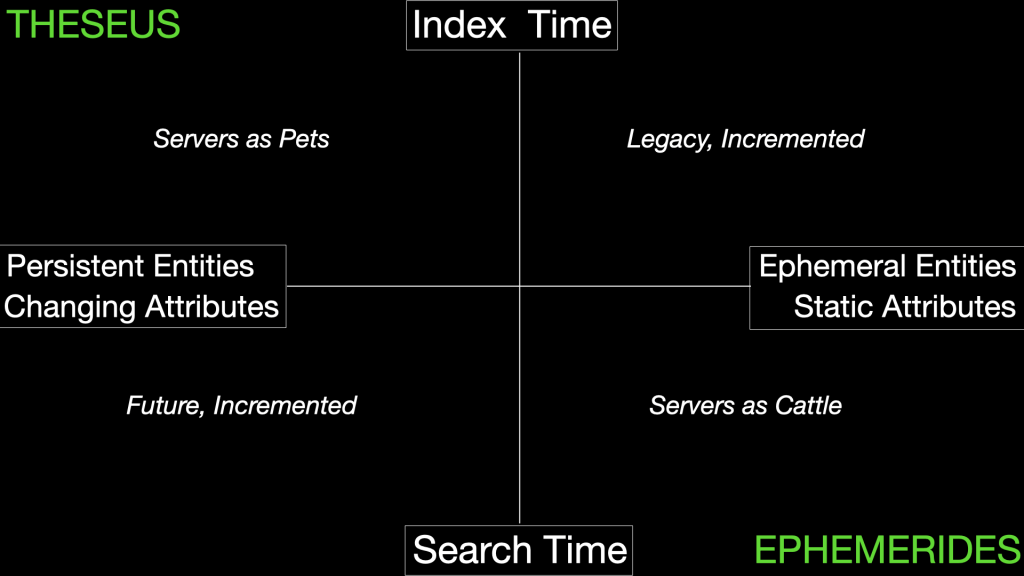
Entities and Attributes
Quadrant models are useful organizing tools. Let’s use one to look at the problem of managing the attributes of entities in systems visibility. I’m not expecting to solve the problem, just usefully describe the playing field. Horizontal axis:* persistent entities with changing attributes* ephemeral entities with static attributes Vertical axis:*…
-

Moving the transformation point of data
There’s a pattern that has become common knowledge, perhaps on its way to received wisdom. Endpoints pass their raw data off to storage as quickly as possible. Analysts then do their work against that storage using map reduced processors, automated and/or ad hoc. This pattern has many benefits and is…
